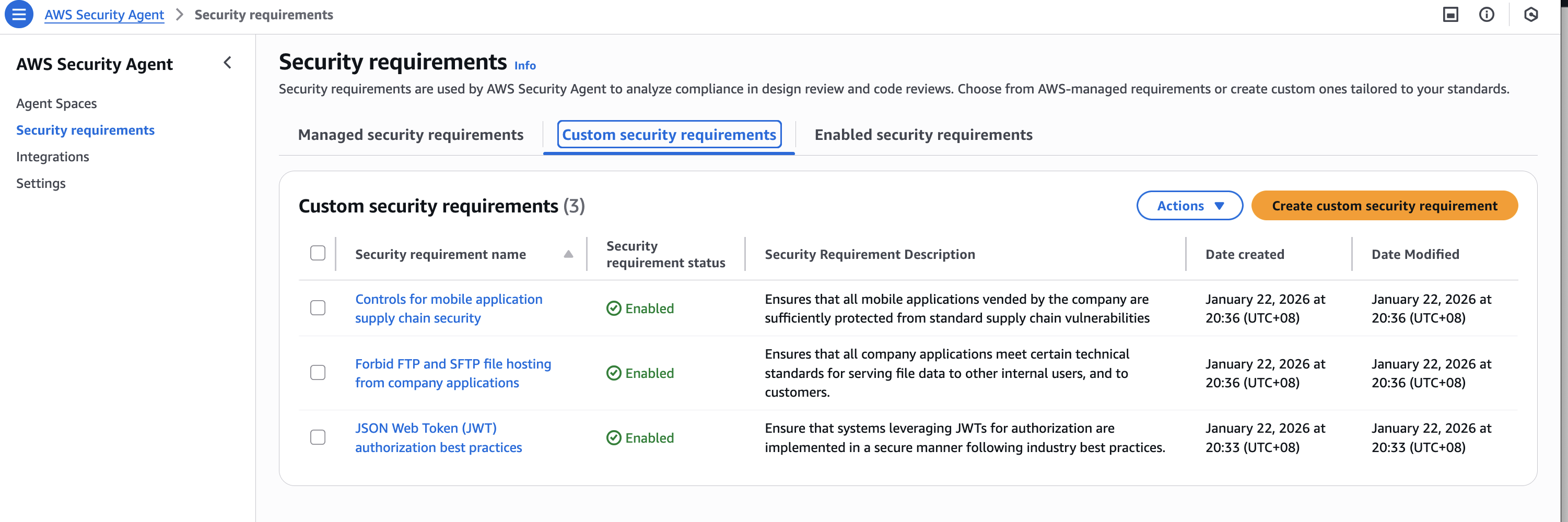
自定义Security requirement
自定义安全要求允许我们使用自己的组织安全策略和标准来指导 AWS Security Agent。通过自定义安全要求,我们可以定义:
-
适用性 - 应评估此安全要求的场景、系统类型或条件
-
合规标准 - 什么构成此安全要求的合规与不合规
-
修复指南 - 可选择提供如何修复违规的指导,包括内部文档或标准的链接
AWS Security Agent 允许我们创建最多 20 个自定义安全要求,以在执行安全设计或代码审查时驱动其行为。我们一次最多可以启用 30 个安全要求,将所有 10 个 AWS 托管安全要求与最多 20 个自定义安全要求结合使用。
创建自定义安全要求
让我们创建一个详细的自定义安全要求,以替换我们在上一页禁用的两个 AWS 托管安全要求。
Juice Shop 利用 JSON Web Tokens (JWTs)(从 OWASP 这里 了解更多)来验证和授权 Web 应用程序中的用户。JWT 是实现无状态安全的常用技术,但要正确集成到生产应用程序中可能具有挑战性。作为 IT 管理员,我们希望确保为组织内使用 JWT 的所有应用程序正确设计和实施 JWT 方案。
首先,导航到安全要求页面上的Custom security requirement选项卡:
点击创建自定义安全要求并填写以下新安全要求的详细信息。完成后,点击页面右下角的创建并启用安全要求按钮。
- 安全要求名称 - JSON Web Token (JWT) authorization best practices
- 描述 - Ensure that systems leveraging JWTs for authorization are implemented in a secure manner following industry best practices.
- 适用性 - Applies to any web application or API system that authorizes both human and programmatic callers using JSON Web Tokens or JWT. JWTs are often issued during authentication and then presented to systems in subsequent requests for purposes of authorization to APIs and resources. JWTs are popular in applications that require security controls holding minimal state, as they can be compatible with many client technologies, server frameworks, and transport protocols. They are commonly integrated with HTTP web applications.
- 合规标准 - A compliant application must explicitly verify all JWTs to protect against token forgery. Applications are clearly non-compliant if they don’t explicitly reject tokens with the “alg” field set to “none”. When verifying any JWT, always require an “alg” field set to “RS256”. This will ensure that an attacker cannot modify a token and have the server believe it has already been verified. Compliant applications must explicitly set audience and issuer fields when creating or signing tokens, and explicitly verify them when receiving tokens.
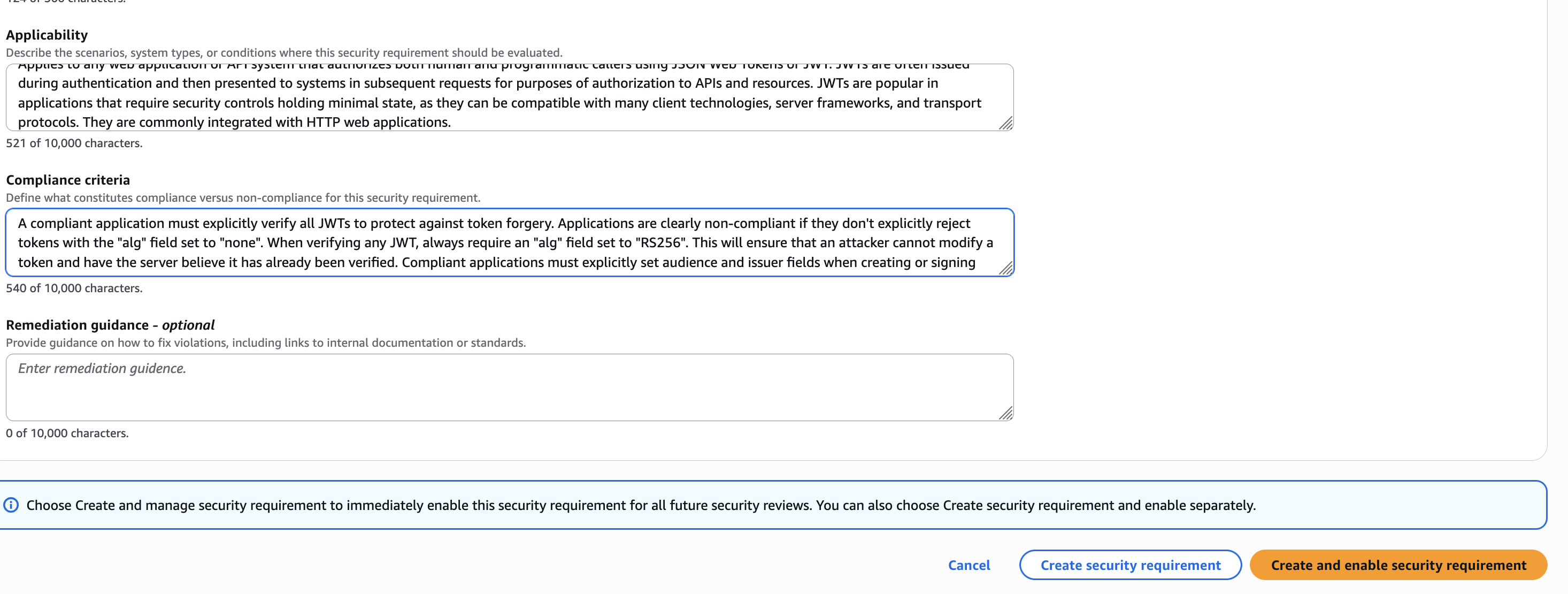
创建完成后的效果:
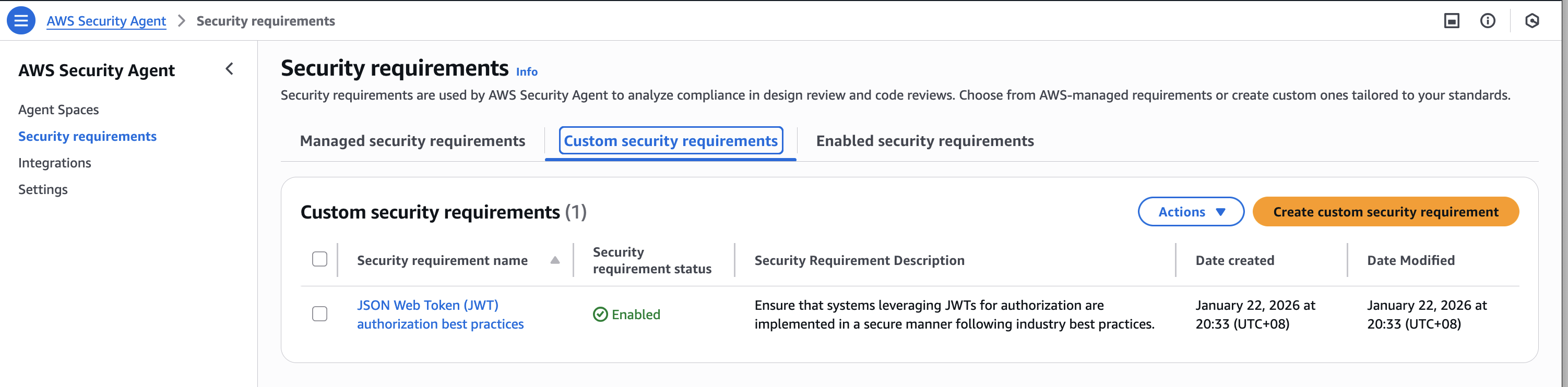
添加其他两个自定义安全要求
我们将创建另外两个自定义安全要求,尽管这两个可能适用/不适用于我们今天正在使用的 Juice Shop 应用程序。安全要求适用于我们的所有 Agent Spaces
创建以下两个自定义安全要求,并确保它们已启用:
禁止公司应用使用 FTP 和 SFTP 文件托管
-
Security requirement name - Forbid FTP and SFTP file hosting from company applications
-
Description - Ensures that all company applications meet certain technical standards for serving file data to other internal users, and to customers.
-
Applicability - Applies to all company applications, including mobile apps (iOS and Android), web applications, API servers.
-
Compliance critera - Any application that supports FTP or SFTP for file hosting is explicitly non-compliant. Any data hosted for public consumption must be accessed through purpose-built APIs, and all internal company documentation and business information must not be made available through a public API or web application. A compliant application uses dedicated APIs for hosting data exclusively, and internal applications may use pre-configured Amazon S3 buckets to share information with internal teams. Company-specific S3 standards follow for compliance. Cloud storage access is approved under the following conditions: allow access to shared S3 buckets for internal-facing applications and users, require least-privilege IAM roles/policies for all S3 access, prohibit use of IAM user access keys & enforce IAM roles with temporary credentials, S3 Block Public Access must be enabled for all S3 buckets and accounts, require any pre-signed URLs with expiration maximum 15 minutes for temporary sharing. Enforce server-side encryption (SSE-KMS) for all objects.
移动应用程序供应链安全控制
-
Security requirement name - Controls for mobile application supply chain security
-
Description - Ensures that all mobile applications vended by the company are sufficiently protected from standard supply chain vulnerabilities
-
Applicability - Applies to all native mobile applications developed by the company, including iOS and Android applications. This requirement specifically does not apply to web applications or server-side API applications.
-
Compliance critera - For an application to be compliant, it must reasonably address every standard that follows: dependency verification - all third-party libraries and SDKs must be obtained from official, verified sources only, maintain a Software Bill of Materials (SBOM) listing all dependencies with versions and checksums, lock dependency versions in package managers (e.g., Podfile.lock for iOS, gradle.lockfile for Android), track code integrity - enable code signing for all application binaries and libraries, use platform-specific integrity checks (iOS: App Attest API, Android: Play Integrity API), verify application signature at runtime to detect tampering, build pipeline security - restrict build environment access to authorized personnel only, use isolated ephemeral build environments, implement automated scanning for known vulnerabilities in dependencies, and establish automated alerts for new CVEs affecting used dependencies.
创建所有三个自定义security requirement后,表格中的自定义安全要求选项卡应如下截图所示: